- Project: Intrusion Detection System
- Duration: 9 months
- Technologies: Blockchain (based on Hyperledger Fabric), Angular 6, Node.js, .NET Core, C#, C++, GoLang, NLP
- Target audience: Small and midsize clinics

Founded by experts in healthcare IT and cybersecurity, Keyqo is a team that applies the newest technology in blockchain to secure patient data by preventing hackers and malicious users from unauthorized access.
THE CASE
Having worked at Epic, the U.S. premier EHR provider, Keyqo’s founders knew the risks that healthcare organizations took with their patient data. To help clinics secure Protected Healthcare Information (PHI) from hacker attacks and data leaks, Mark and Jennifer came up with an innovative blockchain-based product.
Challenge
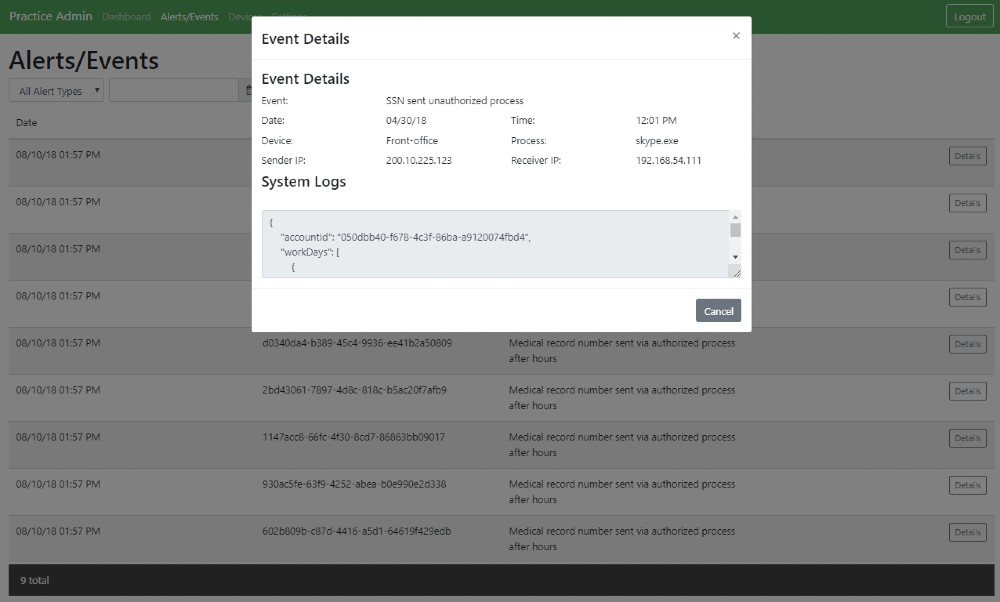
Velvetech was challenged with the development of an intrusion detection system that would monitor user activity and traffic on clinic workstations looking for incidents that could potentially lead to data breaches or hacker attacks. Such early detection would be especially beneficial to small and midsize clinics that otherwise couldn’t afford full-fledged enterprise security solutions like AlienVault.
The blockchain piece of the detection system would be responsible for storing compromised PHI along with logs of suspicious activity. That approach would ensure patient data integrity and security.
Before going into detail about project implementation, let’s quickly capture the core idea of what an intrusion detection system means.
What Is an Intrusion Detection System?
An intrusion detection system, or simply IDS, is a monitoring software application that inspects networks or systems for suspicious activities and generates alerts in case any threats are detected. Apparently, the key aim of IDS is to prevent policy violations, data leaks, and hacker attacks.
The malicious operations can be collected centrally by a security information and event management system, or they can be processed and screened by an authorized person. Either a system or a person apply then filtering techniques to define false attacks or take further actions for protection.
Process
Velvetech had to build the threat detection system end-to-end, starting with its architecture and conceptual design down to all principal functional components. The engineering team came up with the following action plan:
- Develop a stealth monitoring desktop app for sending alerts in case of suspicious activities
- Develop a cloud app for clinics’ personnel to manage the monitoring app and review security alerts
- Develop a cloud app for Keyqo to manage subscribed clinics
Monitoring App

The desktop monitoring app works as a traffic sniffer scanning for malicious activities, like sending unencrypted patient data via unauthorized apps. In addition, it tracks what apps are running and reads their logs. To expedite the development of the sniffer, Velvetech chose an open-source tool called Suricata.
The Keyqo team was very transparent about the requirements for the desktop app:
- Run undetected on Windows and Linux machines
- Require minimum installation steps (plug-and-play solution)
- Be compatible with any EHR system
And that’s precisely what the Velvetech team delivered. The app runs as a service and is not visible to the user. Its installation is as simple as clicking a link, and it’s EHR agnostic because it works on a lower system level, monitoring authorized and unauthorized apps and their logs.
Blockchain Development for Data Protection

To secure PHI and adhere to the HIPAA requirements, the Velvetech team chose to use an open-source blockchain toolset from the Hyperledger Fabric framework. The idea was to get the fact of suspicious activity together with the app logs into a secure, encrypted data vault. And blockchain was the best solution, due to its intrinsic properties: data immutability and out-of-the-box encryption.
What Velvetech’s blockchain development team ended up with can be described as a file system with blockchain-grade encryption, where a ‘file’ is equivalent to an individual smart contract for a practice. This approach ensured that only clinics’ management staff had access to the encrypted data.
Learn more about Blockchain in Healthcare
Natural Language Processing (NLP) for Data Detection

To trigger alerts only for critical security events, the intrusion detection system should have been able to detect the data, and Velvetech opted for an open-source tool by Apache — Apache OpenNLP. Having this NLP toolkit integrated with the solution, clinics could rest assured that their critical patient data won’t be compromised.
Cloud App for Clinic Personnel

The cloud app allows clinic personnel to swiftly deploy the monitoring app to any workstation, set up its alert settings, and review statistics. The development team also built in the granular controls to let users fine-tune the type of alerts the monitoring app generates. That helped reduce the number of false-positive alerts.
In addition, the cloud app can start desktop apps installed on a practice’s machines. An owner can manage the monitoring settings globally and remotely for the whole practice, e.g., which apps are trusted, what data should be monitored, etc.
Cloud App for Keyqo

Finally, Velvetech developed a cloud application for Keyqo to manage clinics, help them work with their cloud app, and monitor subscriptions. Velvetech conducted comprehensive research and presented the most suitable options for Keyqo to choose a subscription service.
After the company opted for one of the presented services, it was only a matter of integrating and testing it with the intrusion detection system. Keyqo appreciated the fact that they didn’t have to invest in developing a hefty subscription management tool from scratch.
Outcome
The result is a cutting-edge technology solution based on blockchain that serves healthcare data information and security. It capitalizes on speed, security, and ease of use, at an ultra-competitive cost resulting in immediate value-add to small and midsize healthcare practices and clinics.
With the intrusion detection system, healthcare organizations are exempted from fines, reputation damage, and legal matters caused by malicious activities of hackers or disgruntled employees. Lastly, patients and employees of medical organizations don’t need to worry about identity theft.
Thanks to everyone at Velvetech for all your hard work in getting this completed. It wasn’t the easiest project, and we couldn’t have done it without you. Jennifer and I look forward to working with you again in the not-too-distant future!
CEO at Keyqo Security
What’s Next
The next phase of the project will involve adding more features, such as localization, exploring more about encrypted traffic as well as the hope of sending notifications to users directly without going through the website to see the displayed results.
Our specialist will contact you to schedule a personalized consultation within one business day.
Velvetech offers complimentary consultations; after which, we will provide you with a proof of concept in just 3 days, an accurate outlook of the cost and timeline of your project and a competitive estimation, and an assembled team – ready to start your project within 7 days.

Proof of Concept in

Start Project within